Data Breach leads to Comcast Customer Data Leak
CyberSecurity Insiders
DECEMBER 26, 2022
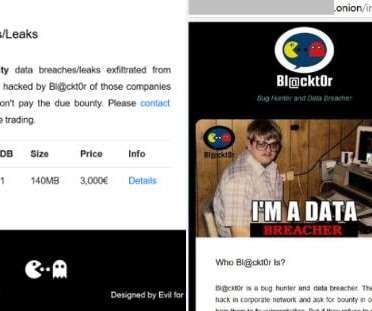
Now, reports are in that the database of the Pennsylvania based digital services provider was hit by a cyber attack leading to a data breach, thus leaking details to hackers. Comcast is yet to officiate the attack, as it is waiting for the preliminary investigation to conclude.



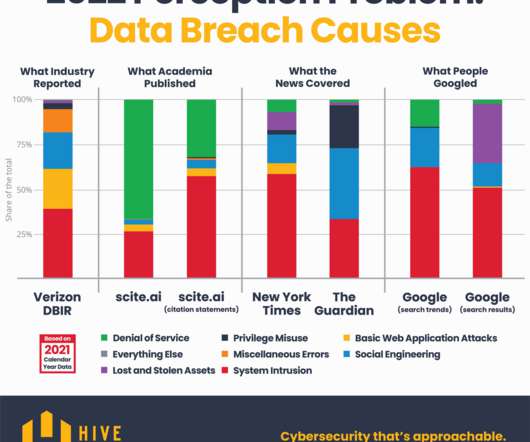

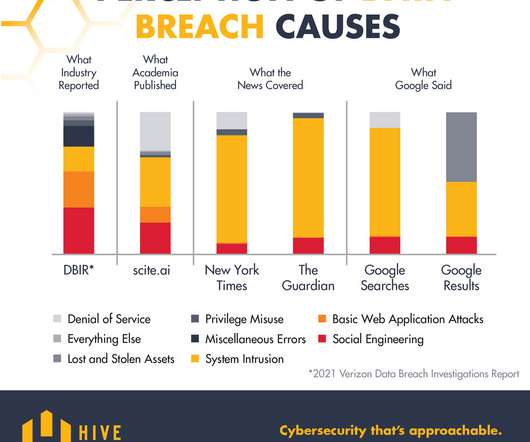
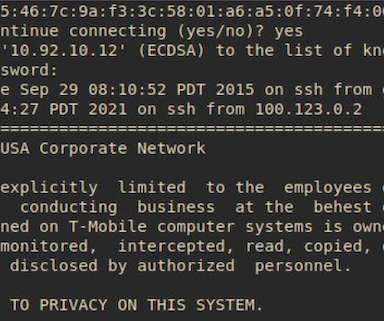

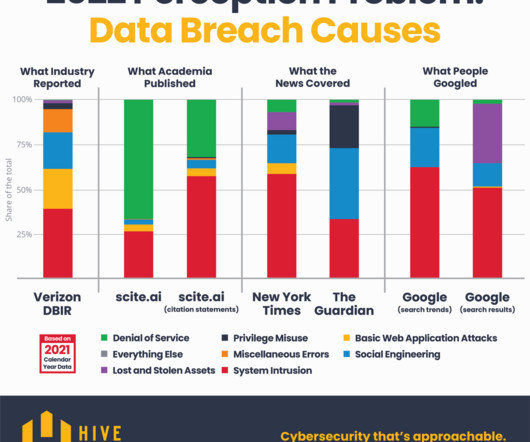


































Let's personalize your content