How to hack Wincor Cineo ATMs to bypass black-box attack protections and withdraw cash
Security Affairs
NOVEMBER 1, 2021
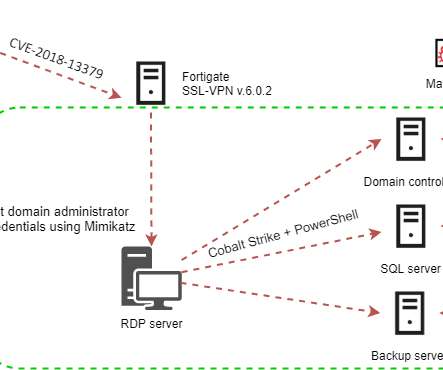
An attacker with access to the dispenser controller’s USB port can install an outdated or modified firmware version to bypass the encryption and make cash withdrawals. An attacker without encryption keys cannot withdraw money. Wincor is currently owned by ATM manufacturer giant Diebold Nixdorf. score of 6.8.











































Let's personalize your content