Hacker leaks passwords for 900+ Pulse Secure VPN enterprise servers
Security Affairs
AUGUST 5, 2020
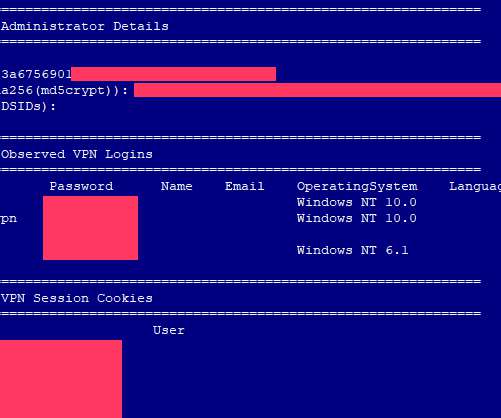
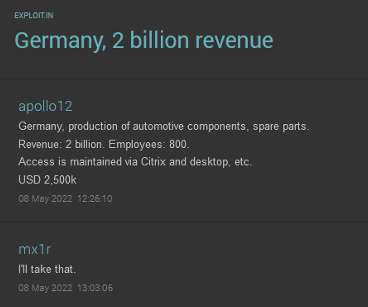
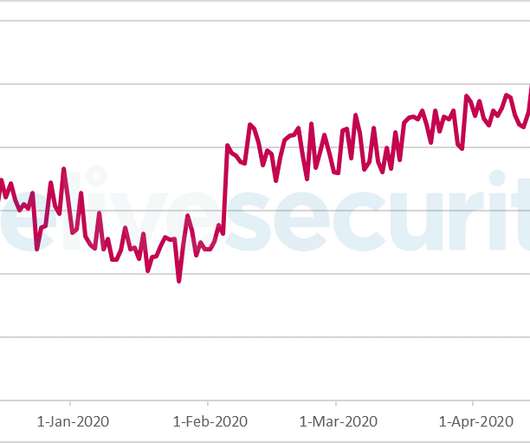
ZDNet reported in exclusive that a list of passwords for 900+ enterprise VPN servers has been shared on a Russian-speaking hacker forum. ZDNet has obtained a copy of the list with the help of threat intelligence firm KELA and verified confirmed the authenticity of the data. reads the advisory. 830) and Germany (789).













































Let's personalize your content