New Linux variant of Clop Ransomware uses a flawed encryption algorithm
Security Affairs
FEBRUARY 7, 2023
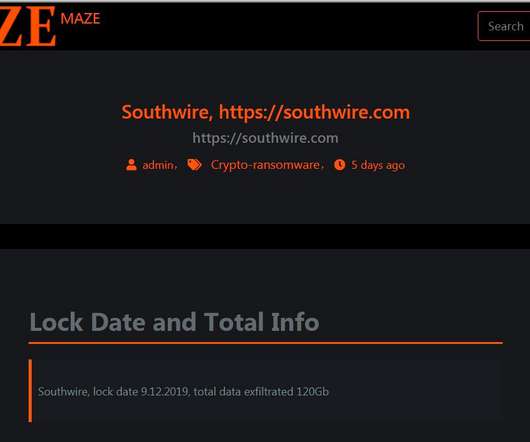
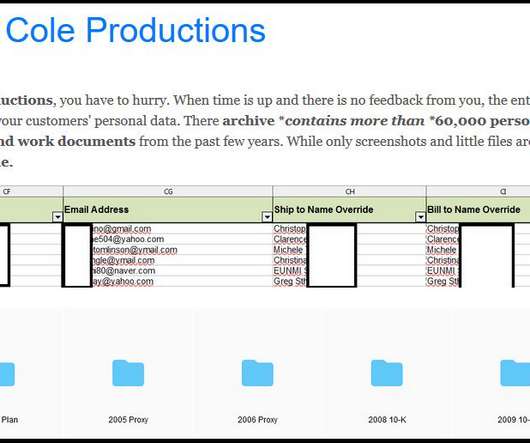
A new Linux variant of the Clop ransomware has been observed in the wild, the good news is that its encryption algorithm is flawed. The researchers noticed that the encryption algorithm implemented in the ELF executable is flawed and can allow victims to decrypt locked files without paying a ransom. ” continues the report.


































Let's personalize your content