Realizing the Benefits of Zero Trust Architecture
SecureWorld News
JULY 21, 2023
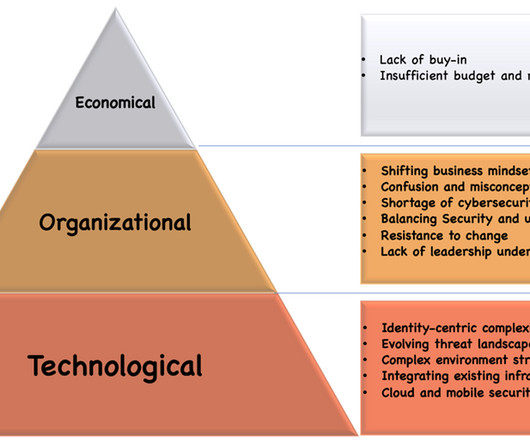
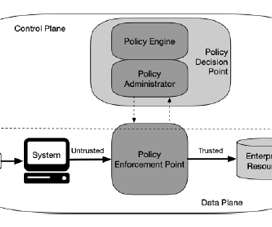
Zero Trust Architecture (ZTA) is gaining significant traction among organizations as a new security framework. A Cybersecurity Insiders survey revealed that as of 2021, 72% of organizations have either implemented or are in the process of adopting Zero Trust Architecture.








































Let's personalize your content