New Cring ransomware deployed targeting unpatched Fortinet VPN devices
Security Affairs
APRIL 7, 2021
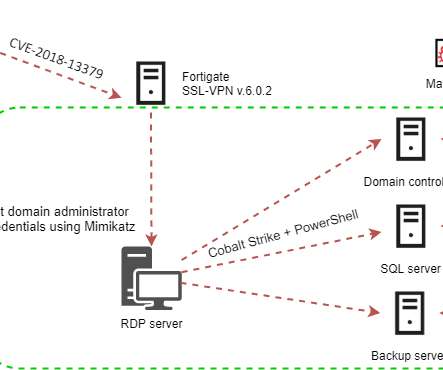
Attackers are actively exploiting the CVE-2018-13379 flaw in Fortinet VPN to deploy the Cring ransomware to organizations in the industrial sector. This ransomware encrypts data from victims with AES-256 + RSA-8192 and then demands a ~ 2 BTC ransom to get the files back. . SecurityAffairs – hacking, Fortinet VPN).




















Let's personalize your content