Fla. Man Charged in SIM-Swapping Spree is Key Suspect in Hacker Groups Oktapus, Scattered Spider
Krebs on Security
JANUARY 30, 2024
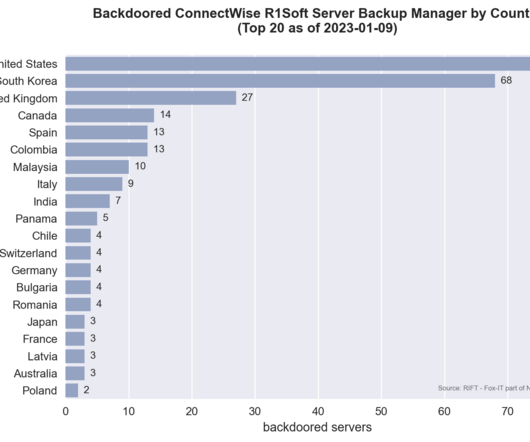
technology companies during the summer of 2022. stole at least $800,000 from at least five victims between August 2022 and March 2023. 2022 that an intrusion had exposed a “limited number” of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials.















































Let's personalize your content