LW ROUNDTABLE — How 2024’s cyber threats will transform the security landscape in 2025
The Last Watchdog
DECEMBER 16, 2024
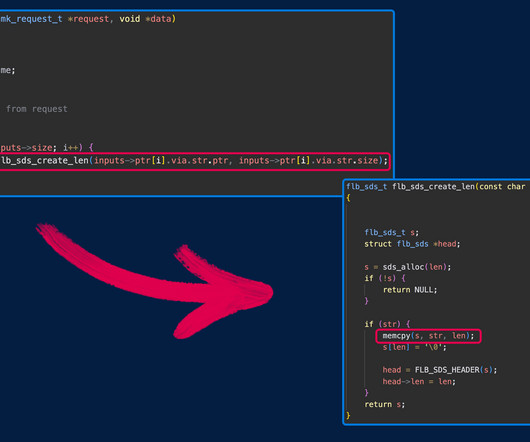
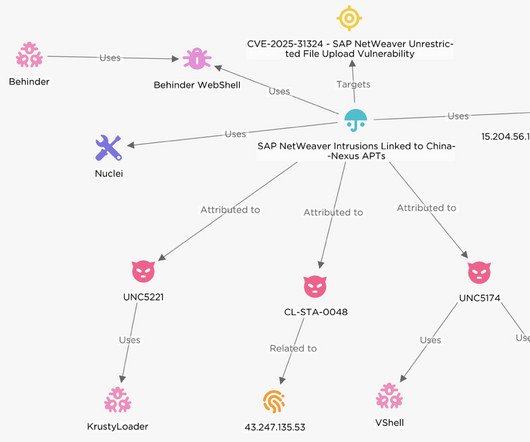
Continuing our look back at 2024, part two of Last Watchdogs year-ender roundtable turns its focus to emerging threats vs. evolving defense tactics. Sundaresan Bindu Sundaresan , Cybersecurity Director, LevelBlue In 2025, cybercriminals will exploit supply chain vulnerabilities, ransomware, IoT botnets, and AI-driven phishing.



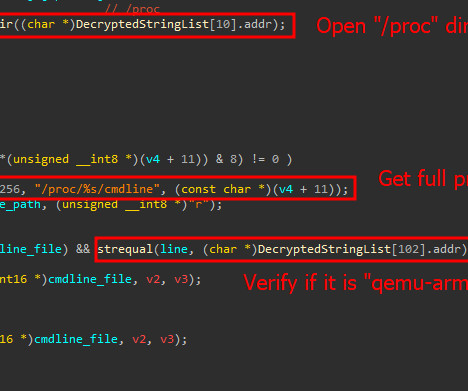

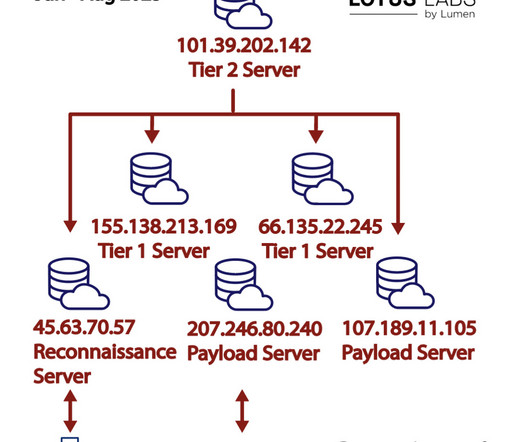











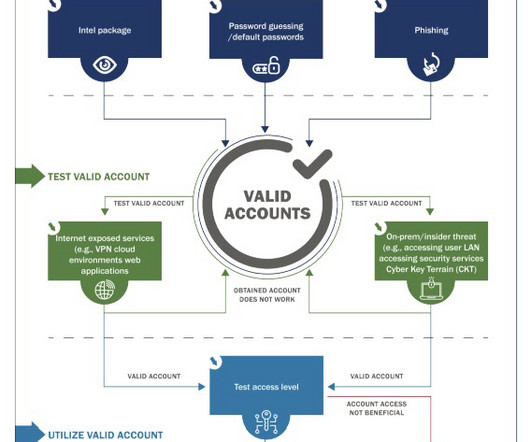


























Let's personalize your content