‘The Manipulaters’ Improve Phishing, Still Fail at Opsec
Krebs on Security
APRIL 3, 2024
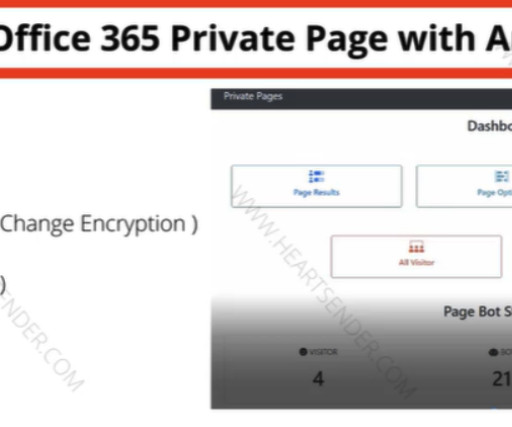
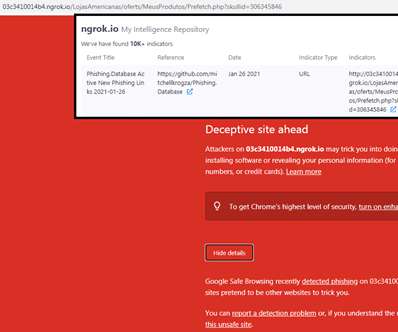
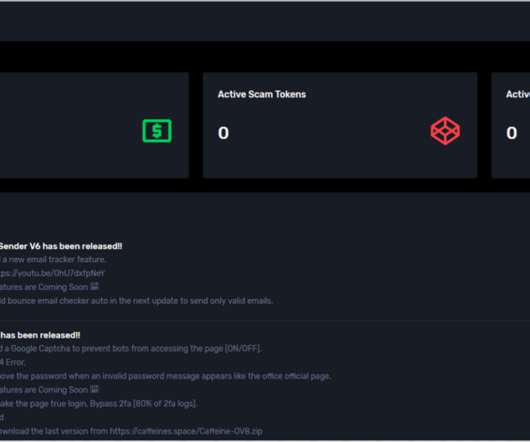
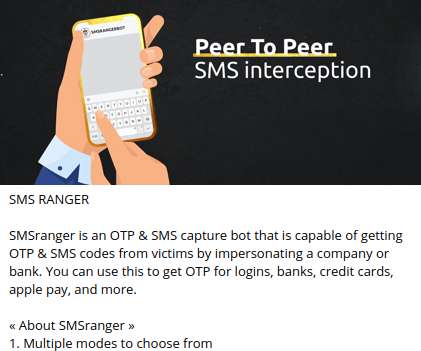
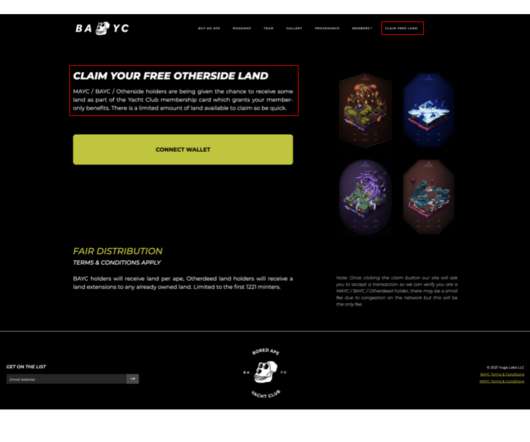
Roughly nine years ago, KrebsOnSecurity profiled a Pakistan-based cybercrime group called “ The Manipulaters ,” a sprawling web hosting network of phishing and spam delivery platforms. Manipulaters advertisement for “Office 365 Private Page with Antibot” phishing kit sold on the domain heartsender,com.





































Let's personalize your content