NIST’s ransomware guidelines look a lot like cyber resilience
Webroot
AUGUST 27, 2021
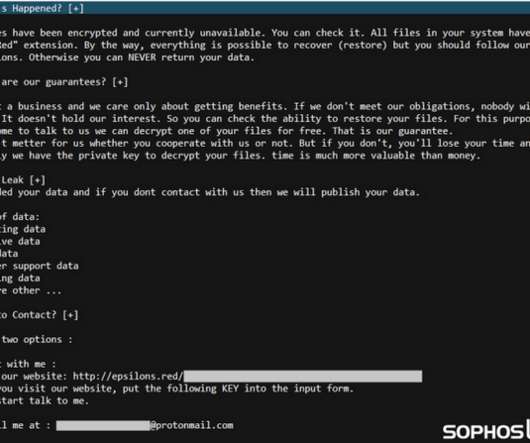
Nevertheless, the report took the danger presented by ransomware to both businesses and global security for granted. While natural disasters and unplanned outages were once the focus of these contingency plans, ransomware’s current popularity is another reason to ensure backup and recovery are accounted for.

































Let's personalize your content