Securing APIs: Application Architecture Disrupted
Security Boulevard
MARCH 5, 2021
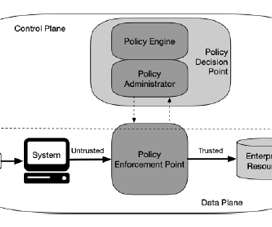
We’re happy to introduce our latest blog series called Securing APIs: The New Application Attack Surface. Let’s give thanks to Salt Security as the potential licensee of this blog series before we get started. Application Architecture Today. As we get started, let’s go through how we see application architecture evolving.












































Let's personalize your content