Information risk and security for professional services
Notice Bored
APRIL 20, 2022
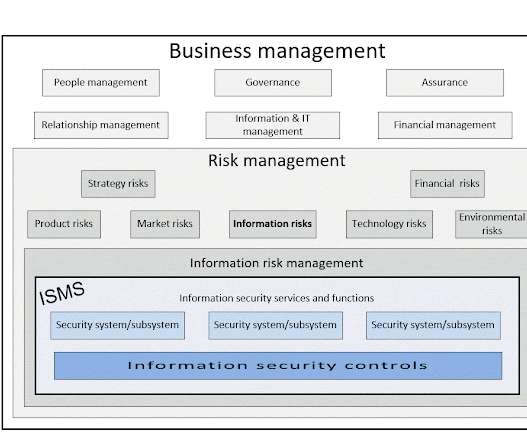
Professional services are information-centric: information is the work product , the purpose, the key deliverable. Through assignments, jobs, projects or tasks, professional services clients and providers exchange, generate and utilize information.


















Let's personalize your content