Multi-Factor is incomplete without backup codes
CyberSecurity Insiders
JANUARY 10, 2022
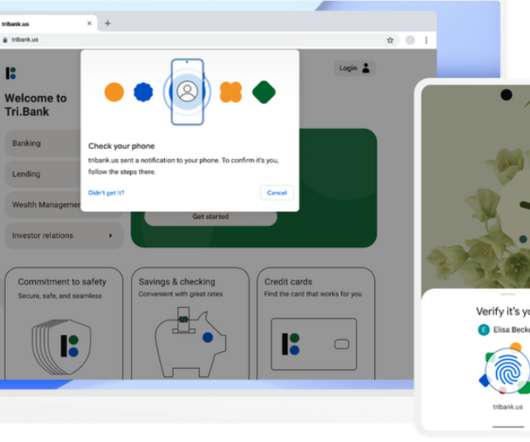
I was logging into one of my favorite online shopping sites the other day, and, as with all my other sites, I was presented with the multi-factor authentication prompt to complete the login process. The problem is that the registered phone number is attached to the same dead phone that contains the authenticator application.













































Let's personalize your content