An educational robot security research
SecureList
FEBRUARY 27, 2024
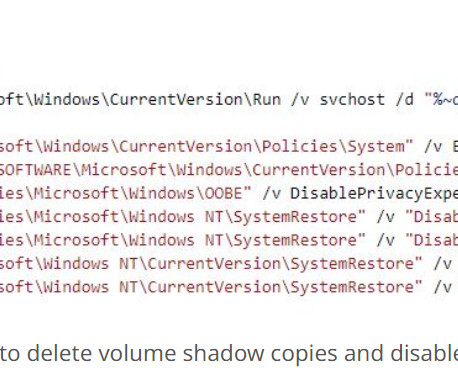
” For instance, educational robots that connect to the internet and support video calls. Subject of the study: educational robot The toy is designed to educate and entertain children; it is an interactive device running the Android operating system. This was the first security-related issue we discovered.





































Let's personalize your content