Hacking Grindr Accounts with Copy and Paste
Troy Hunt
OCTOBER 2, 2020
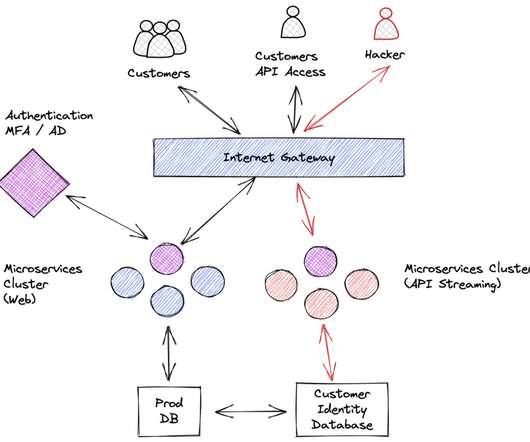
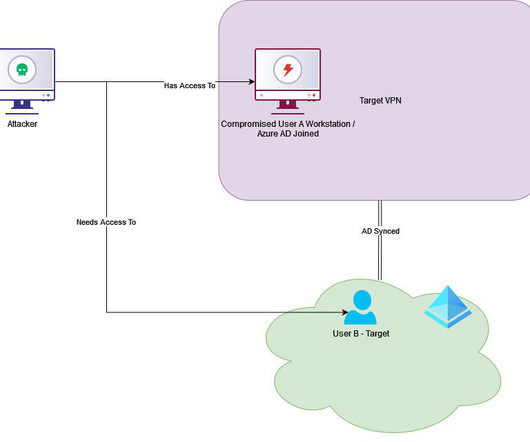
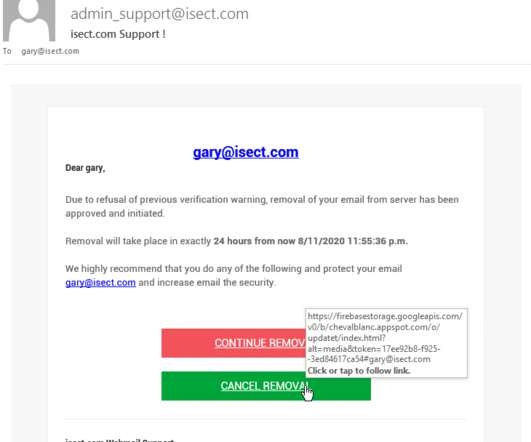
The vulnerability allow an attacker to hijack any account. I asked for technical detail so I could validated the authenticity of his claim and the info duly arrived. On a surface of it, things looked bad: complete account takeover with a very trivial attack. Full account takeover.












































Let's personalize your content