Top 3 API Leaks Identified by Cybersecurity & InfoSec Experts
Security Boulevard
APRIL 8, 2024
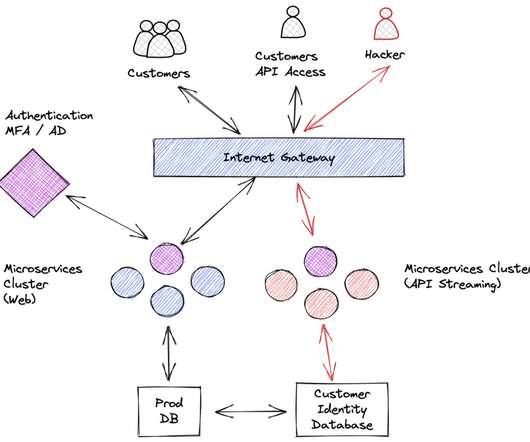
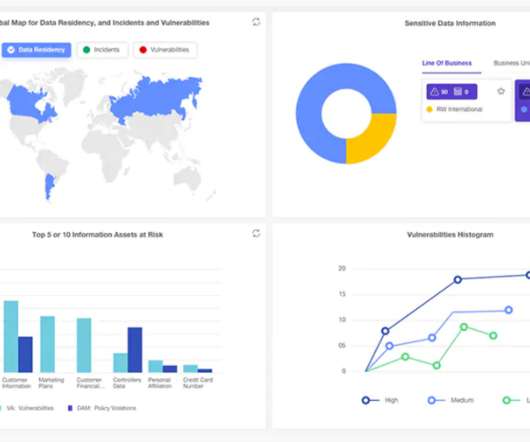
Due to their inherent complexity and the dynamic nature of software ecosystems, common vulnerabilities include inadequate authentication mechanisms [.] The post Top 3 API Leaks Identified by Cybersecurity & InfoSec Experts appeared first on Wallarm.










































Let's personalize your content