DarkSide Ransomware Gang Quits After Servers, Bitcoin Stash Seized
Krebs on Security
MAY 14, 2021
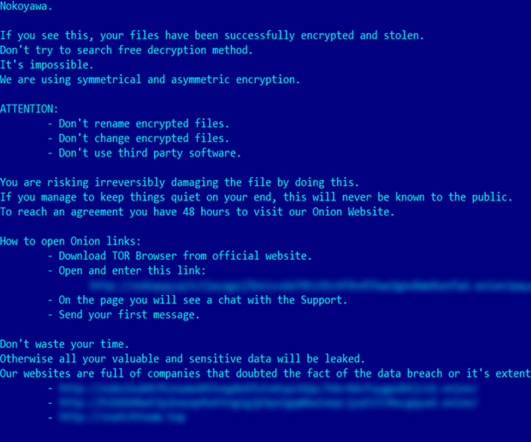
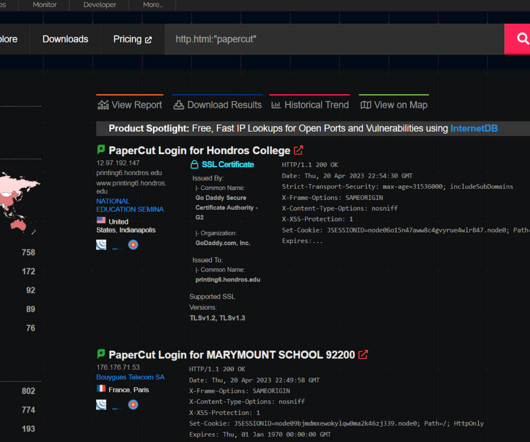
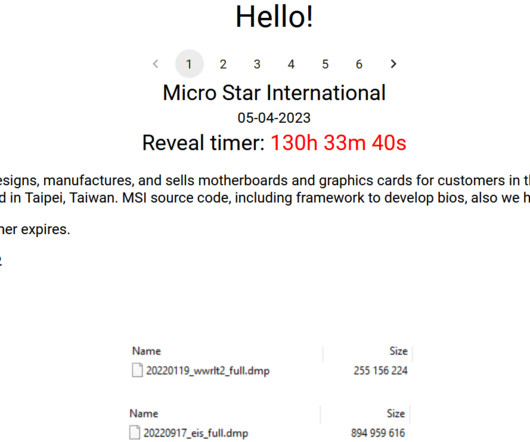
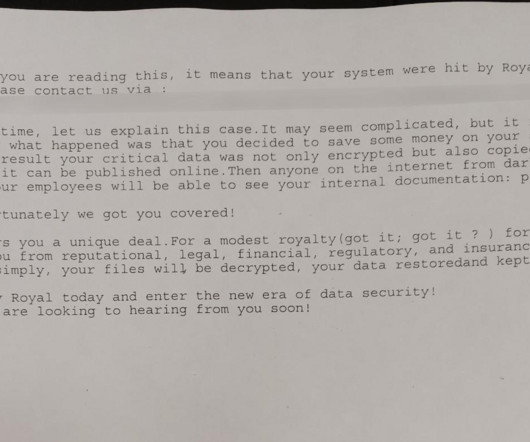
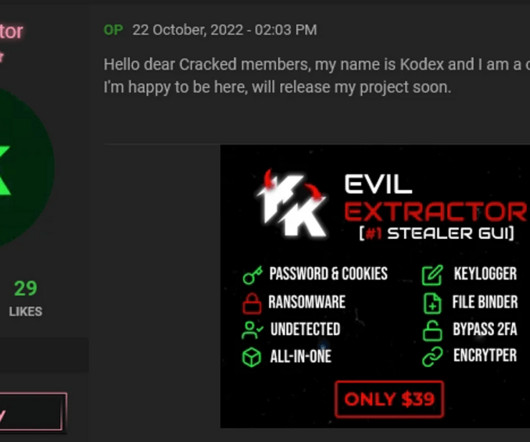
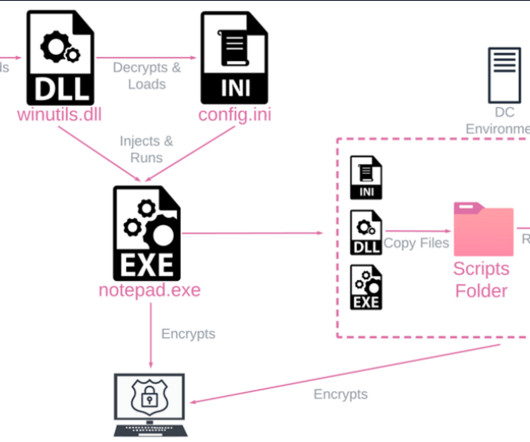
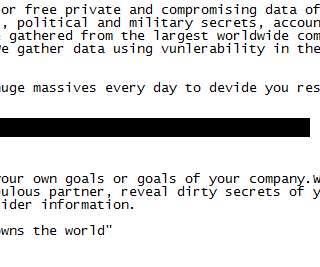
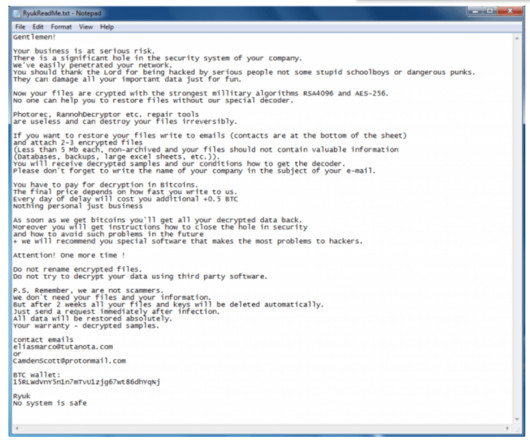
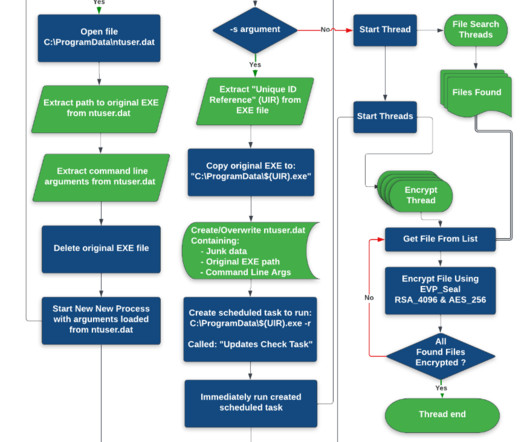
The DarkSide ransomware affiliate program responsible for the six-day outage at Colonial Pipeline this week that led to fuel shortages and price spikes across the country is running for the hills. The DarkSide message includes passages apparently penned by a leader of the REvil ransomware-as-a-service platform.

















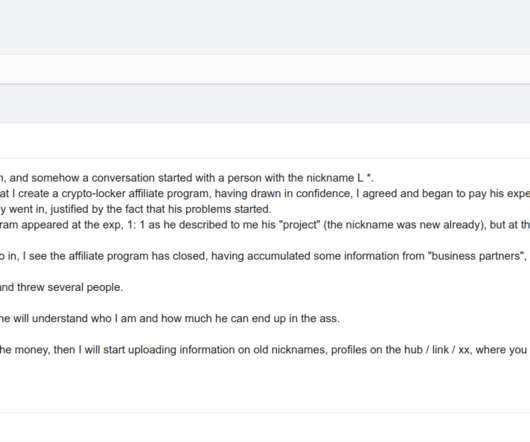


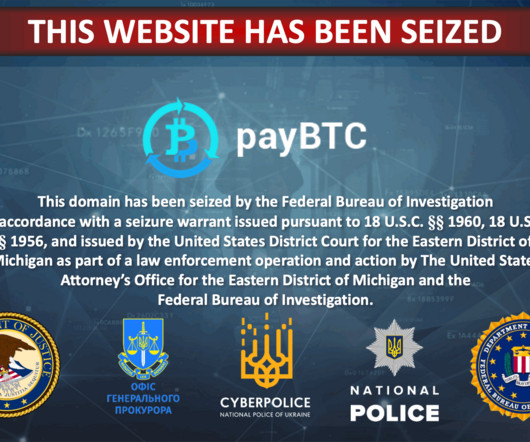

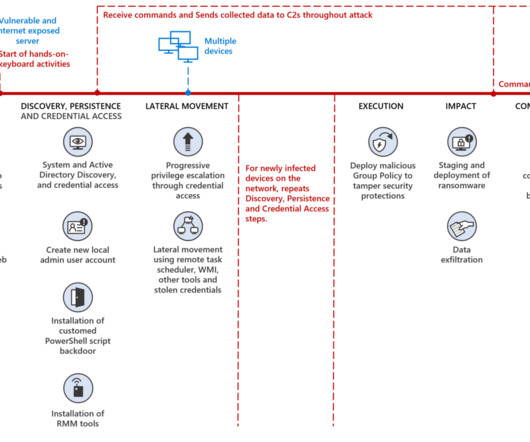










Let's personalize your content