Roaming Mantis uses new DNS changer in its Wroba mobile malware
Security Affairs
JANUARY 22, 2023
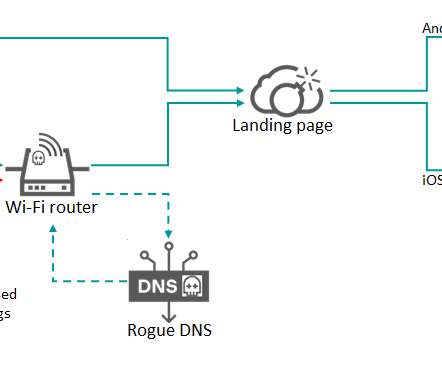
Roaming Mantis threat actors were observed using a new variant of their mobile malware Wroba to hijack DNS settings of Wi-Fi routers. Researchers from Kaspersky observed Roaming Mantis threat actors using an updated variant of their mobile malware Wroba to compromise Wi-Fi routers and hijack DNS settings.











































Let's personalize your content