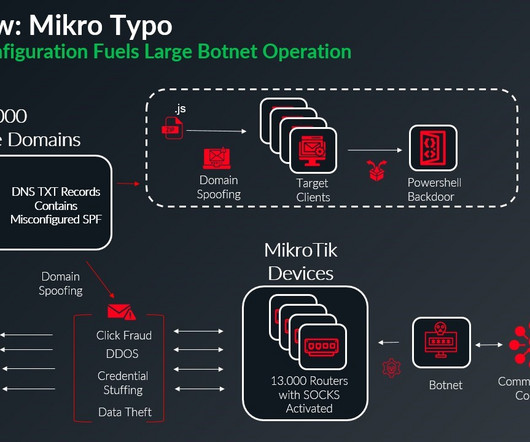
MikroTik botnet relies on DNS misconfiguration to spread malware
Security Affairs
JANUARY 16, 2025
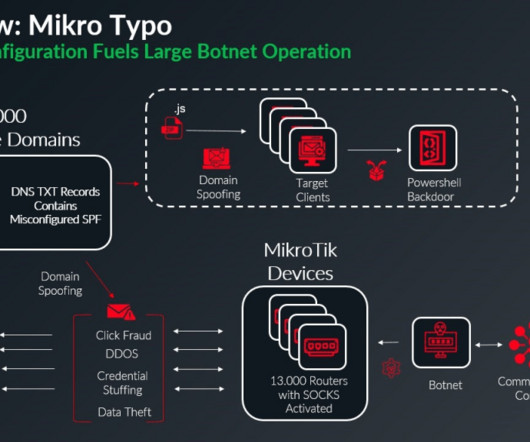
Researchers discovered a 13,000-device MikroTik botnet exploiting DNS flaws to spoof 20,000 domains and deliver malware. Infoblox researchers discovered a botnet of 13,000 MikroTik devices that exploits DNS misconfigurations to bypass email protections, spoof approximately 20,000 domains, and deliver malware.









































Let's personalize your content