For 2nd Time in 3 Years, Mobile Spyware Maker mSpy Leaks Millions of Sensitive Records
Krebs on Security
SEPTEMBER 4, 2018
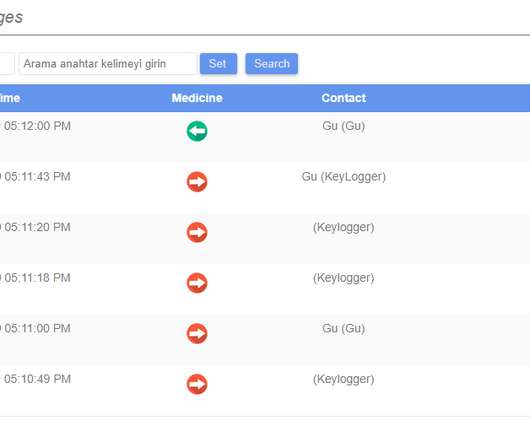
Less than a week ago, security researcher Nitish Shah directed KrebsOnSecurity to an open database on the Web that allowed anyone to query up-to-the-minute mSpy records for both customer transactions at mSpy’s site and for mobile phone data collected by mSpy’s software. The database required no authentication. WHO IS MSPY?
















































Let's personalize your content