Social Engineering 101: What It Is & How to Safeguard Your Organization
Duo's Security Blog
DECEMBER 14, 2023
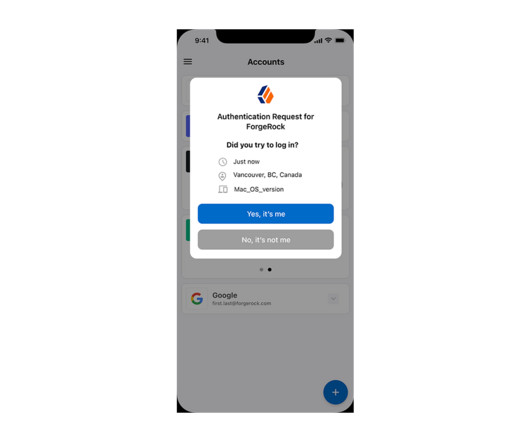
A few days later, John finds himself locked out of his account, and quickly learns that the password reset link he clicked earlier did not come from his company. He took the steps needed to keep his account safe by following the directions from his IT team. What is social engineering? John is a diligent employee.













































Let's personalize your content