How Hackers Create Free Wi-Fi Captive Portal To Steal Social Media Accounts !
Hacker's King
DECEMBER 4, 2023
Hackers can also take advantage of this and trap hundreds of victims at once and steal their credentials of social accounts. So let me give you a short overview of what actually a hacker does to create a fake Wi-Fi captive to steal social media accounts. In Schools, colleges, Railway Stations, etc.

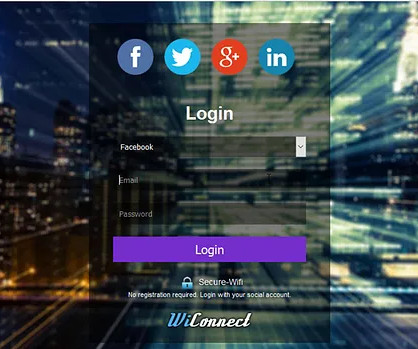


































Let's personalize your content