Facebook Is Using Your Two-Factor Authentication Phone Number to Target Advertising
Schneier on Security
OCTOBER 2, 2018
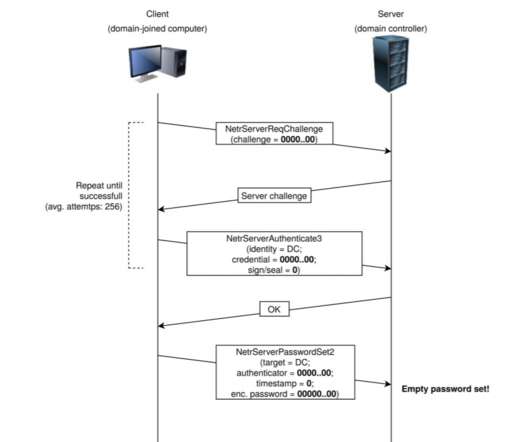
From Kashmir Hill : Facebook is not content to use the contact information you willingly put into your Facebook profile for advertising. So users who want their accounts to be more secure are forced to make a privacy trade-off and allow advertisers to more easily find them on the social network.

































Let's personalize your content