DRAGONBLOOD flaws allow hacking WPA3 protected WiFi passwords
Security Affairs
AUGUST 3, 2019
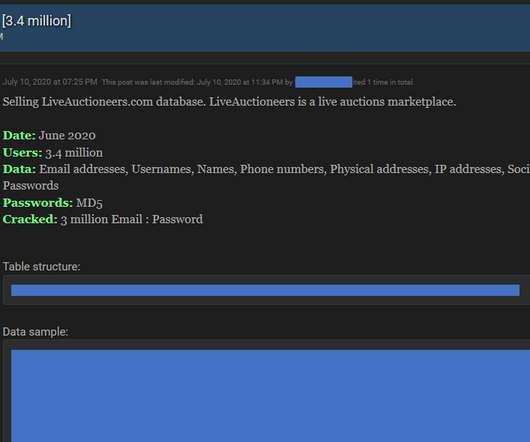
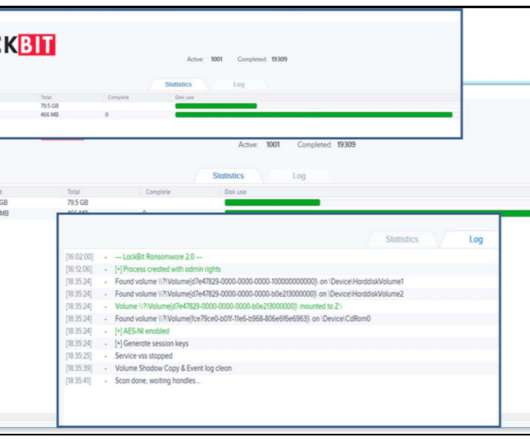
Dragonblood researchers found two new weaknesses in WPA3 protocol that could be exploited to hack WPA3 protected WiFi passwords. passwords. A group of researchers known as Dragonblood (Mathy Vanhoef and Eyal Ronen ) devised new methods to hack WPA3 protected WiFi passwords by exploiting two new vulnerabilities dubbed Dragonblood flaws.




































Let's personalize your content