UK Fintech company Finastra hit by a cyber attack
Security Affairs
MARCH 21, 2020
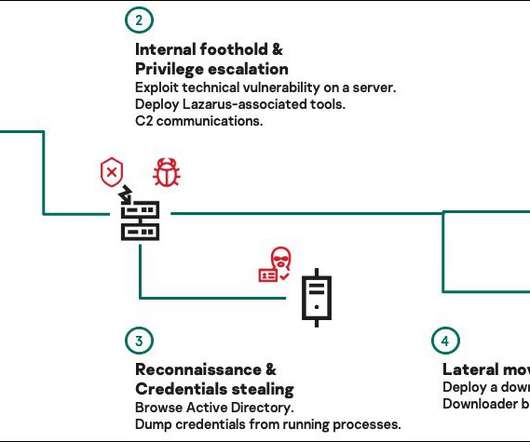
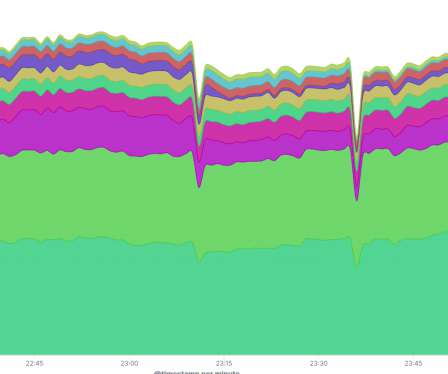
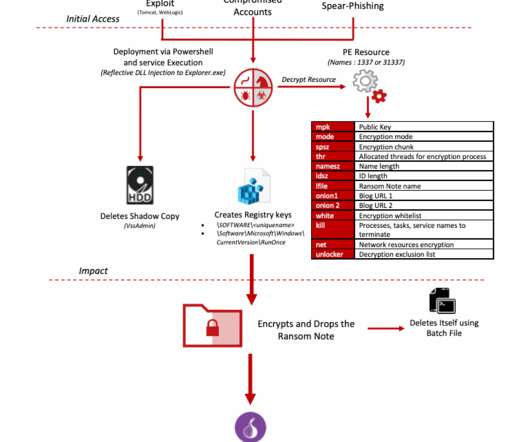
.” Experts from cyber-security firm Bad Packets speculate attackers might have exploited the CVE-2019-11510 vulnerability to compromise unpatched Pulse Secure VPN servers at the Fintech firm. . Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Travelex deja vu? Pierluigi Paganini.











































Let's personalize your content