Lumma/Amadey: fake CAPTCHAs want to know if you’re human
SecureList
OCTOBER 29, 2024
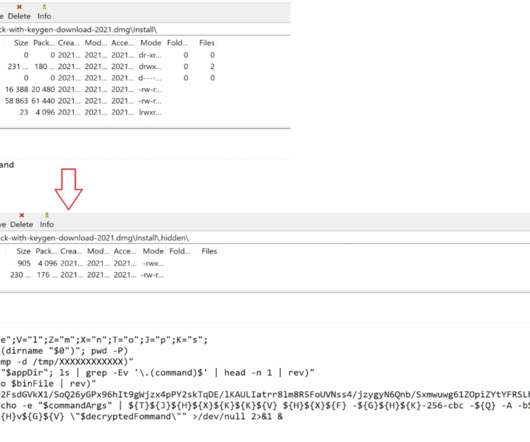
Our recent research into the adware landscape revealed that this malicious CAPTCHA is spreading through a variety of online resources that have nothing to do with games: adult sites, file-sharing services, betting platforms, anime resources, and web apps monetizing through traffic. One of the modules can also take screenshots.















































Let's personalize your content