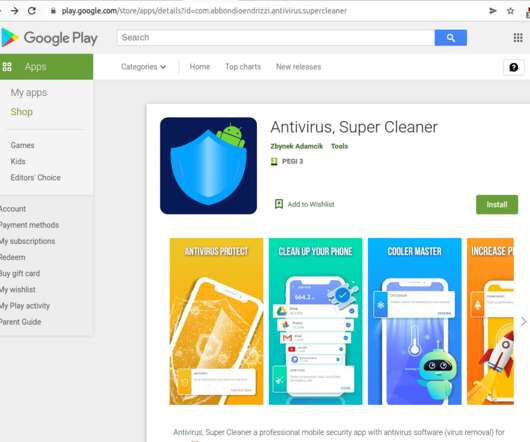
SharkBot Malware Poses as Android Antivirus
Heimadal Security
MARCH 7, 2022
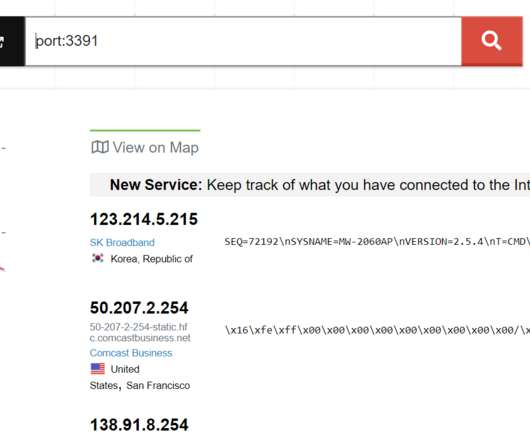
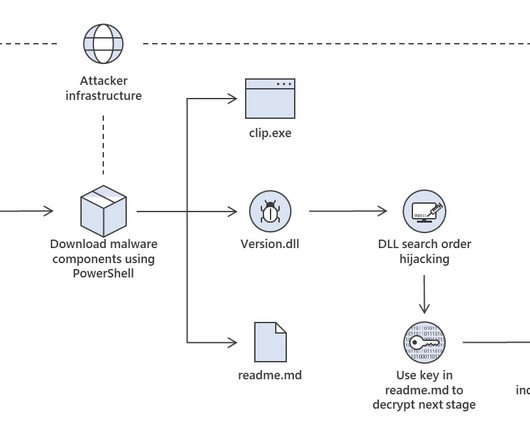
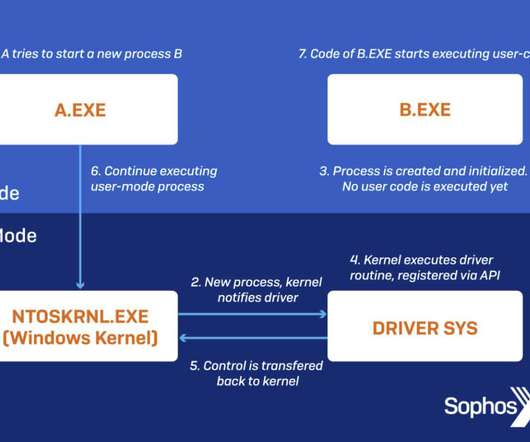
One of the primary objectives of SharkBot is to start money transfers from hacked devices via the Automatic Transfer Systems (ATS) approach, which circumvents multi-factor authentication measures. Identification and authentication systems are used to impose user identity verification […].













































Let's personalize your content