7 Internet Safety Tips for Safer Internet Browsing
Identity IQ
AUGUST 19, 2023
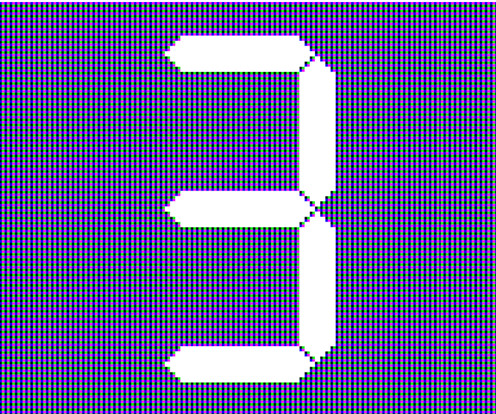
7 Internet Safety Tips for Safer Internet Browsing IdentityIQ With the internet, we can access vast amounts of information with only a click or tap. This year, the total number of internet users worldwide reached 5.18 And as immense as the internet is, so are the risks. Many threats lurk in its corners.


















































Let's personalize your content