What is a Cyberattack? Types and Defenses
eSecurity Planet
JUNE 16, 2022
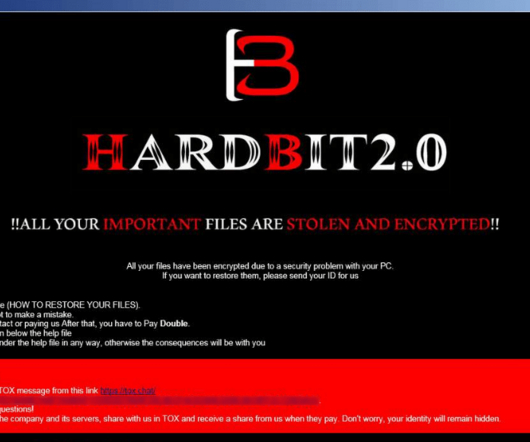
Also read: Best Antivirus Software of 2022. Also read: How to Recover From a Ransomware Attack Best Ransomware Removal Tools Best Ransomware Removal and Recovery Services Best Backup Solutions for Ransomware Protection. Crimeware and spyware. Backup and encryption. So keeping backups offline is of paramount importance.


























Let's personalize your content