Backdoors and Miners Amid eScan Antivirus Backdoor Exploit
Security Boulevard
MAY 10, 2024
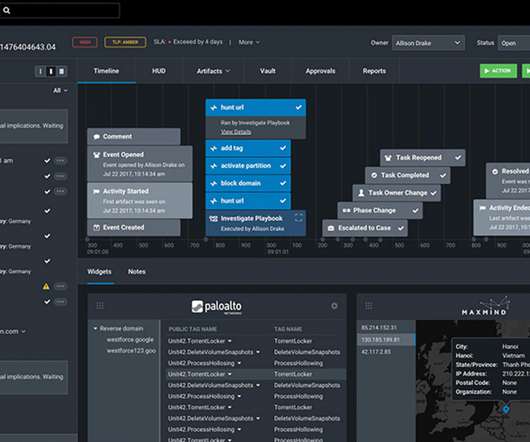
Recently, a wave of malware attacks has surfaced, exploiting vulnerabilities in the update mechanism of the eScan antivirus software. This eScan antivirus backdoor exploit distributes backdoors and cryptocurrency miners, such as XMRig, posing a significant threat to large corporate networks.

































Let's personalize your content