New Cring ransomware deployed targeting unpatched Fortinet VPN devices
Security Affairs
APRIL 7, 2021
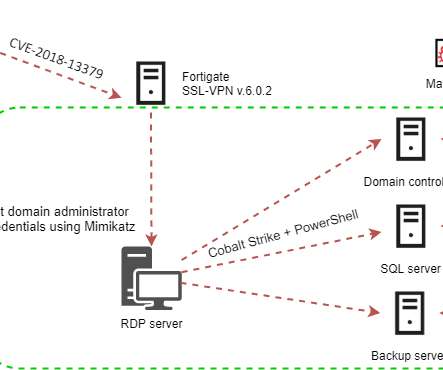
Attackers are actively exploiting the CVE-2018-13379 flaw in Fortinet VPN to deploy the Cring ransomware to organizations in the industrial sector. The Cring ransomware appeared in the threat landscape in January, it was first reported by Amigo_A and the CSIRT team of Swisscom. ” reads the post published by Kaspersky.













































Let's personalize your content