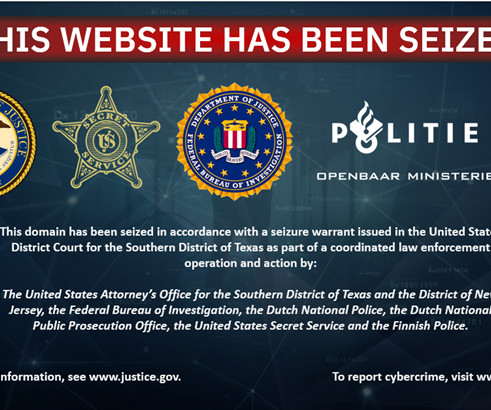
Police took down several popular counter-antivirus (CAV) services, including AvCheck
Security Affairs
JUNE 2, 2025
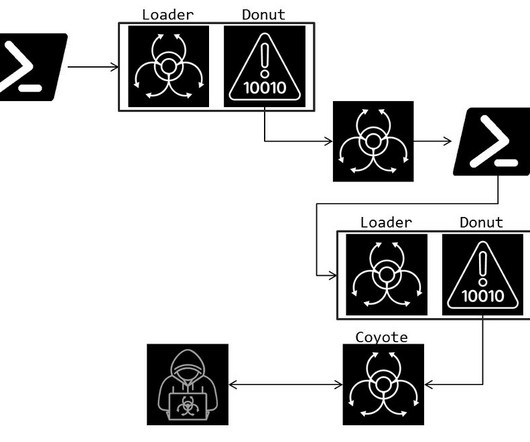
“Crypting is the process of using software to make malware difficult for antivirus programs to detect,” the DoJ said. “The seized domains offered services to cybercriminals, including counter-antivirus (CAV) tools.” ” reads the press release published by DoJ. Dutch police, in coordination with U.S.






































Let's personalize your content