Joker malware infected 538,000 Huawei Android devices
Security Affairs
APRIL 11, 2021
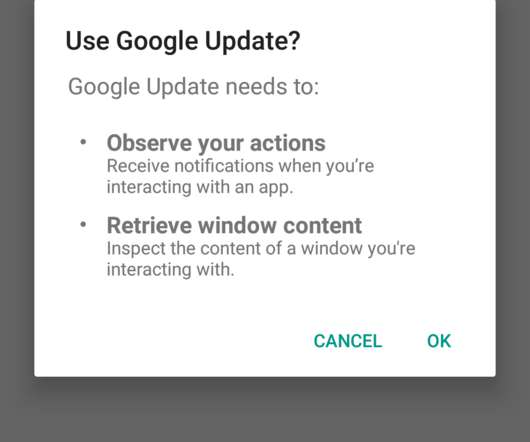
More than 500,000 Huawei users have been infected with the Joker malware after downloading apps from the company’s official Android store. More than 500,000 Huawei users were infected with the Joker malware after they have downloaded tainted apps from the company’s official Android store. aliyuncs.com/ Android.Joker.531




















Let's personalize your content