Ransomware realities in 2023: one employee mistake can cost a company millions
Security Affairs
OCTOBER 17, 2023
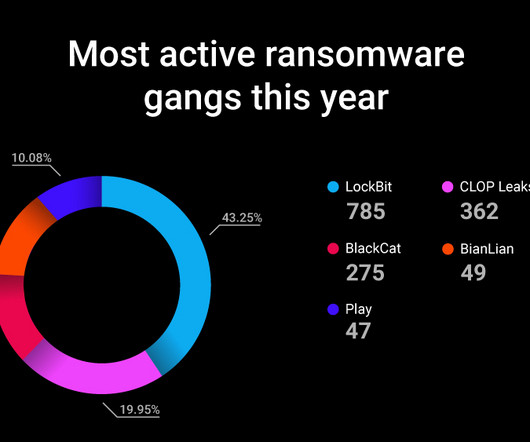
With 85% of campaigns targeting victims with phishing emails containing malicious links, another form of a social engineering attack, education and cyber vigiliance remain a high priority. Why should employers educate employees about cyber security? This method was identified as vishing – a voice-based phishing attack.































Let's personalize your content