3 Ways Software Licensing Eliminates Vulnerabilities to Enhance Security
IT Security Guru
NOVEMBER 16, 2022
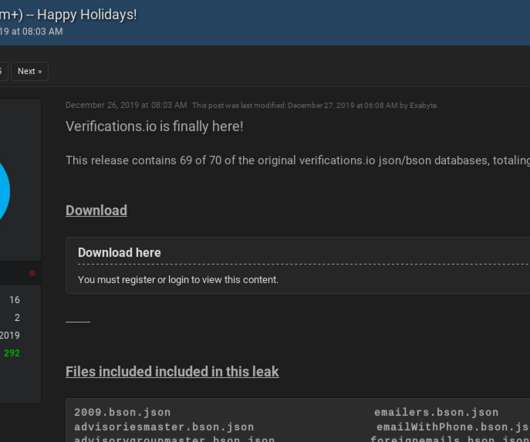
While you may entertain the idea of using free tools, unlicensed software can expose your organization to various security and financial risks. To enhance security and efficiency, software licensing is vital in today’s business landscape. Here are various ways licensing ensures better security.
















































Let's personalize your content