SolarWinds Security Event Manager – SIEM Product Overview and Insight
eSecurity Planet
FEBRUARY 6, 2023
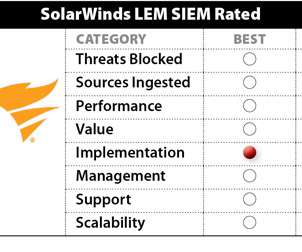
SolarWinds Security Event Manager (SEM) 2022.4 SEM ships with hundreds of predefined correlation rules, including authentication, change management, network attacks, and more. SolarWinds SEM supports a variety of event sources, including nonevent data sources that can be integrated into its analytics and correlation rules.















































Let's personalize your content