Check Point Warns of Hackers Targeting Its Remote Access VPN
SecureWorld News
MAY 28, 2024
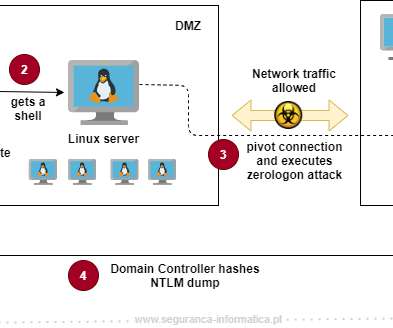
In the advisory , Check Point says the attackers are targeting security gateways with old local accounts using insecure password-only authentication, which should be used with certificate authentication to prevent breaches. "We Switching from weak authentication to stronger authentication has multiple benefits.










































Let's personalize your content