LW ROUNDTABLE: Cybersecurity takeaways of 2023 — and what’s ahead in 2024 ( part 1)
The Last Watchdog
DECEMBER 12, 2023
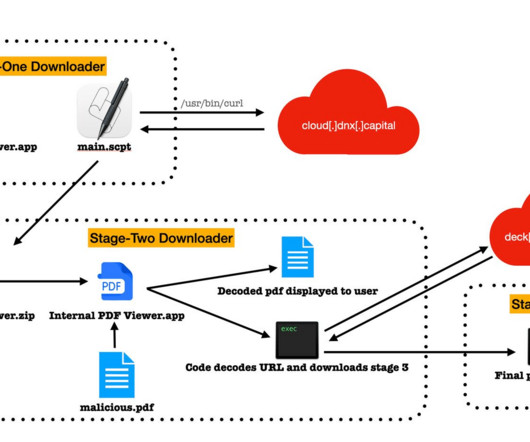
Implementing a Zero Trust architecture involves verifying every attempt to access the system. Dick O’Brien , Principal Intelligence Analyst, Symantec Threat Hunters O’Brien The Snakefly cybercrime group (aka Clop) advanced extortion attacks in 2023 with their exploitation of the MOVEit Transfer vulnerability.














































Let's personalize your content