How to evolve your organization into a data-centric security architecture
CyberSecurity Insiders
DECEMBER 21, 2021
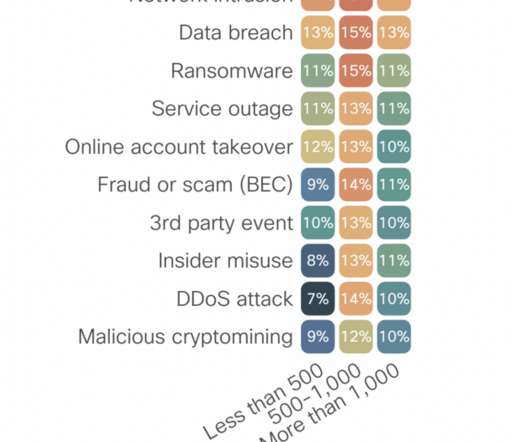
Unfortunately, breaches remain a viable outcome, and some cell carriers have even started to provide breach alerts to their clients because they are within the realm of possibility. If you discover a data breach, you should contact your IT department and follow their instructions.


















































Let's personalize your content