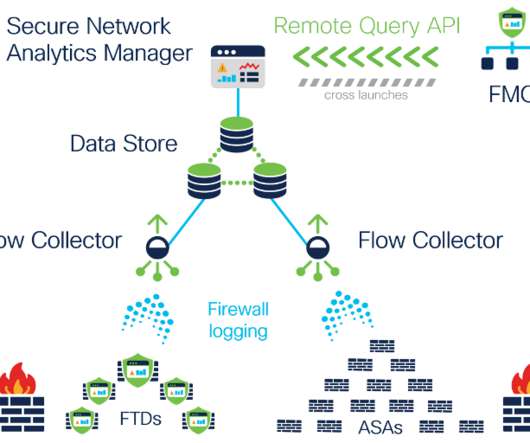
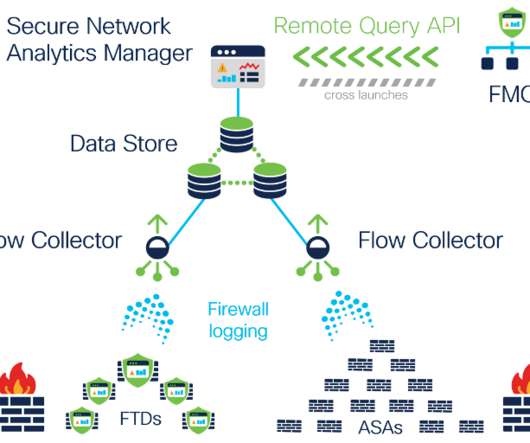
Introducing continuous remote worker visibility and expanded data collection with Secure Network Analytics Release 7.3.2
Cisco Security
JUNE 1, 2021
However, back then, although these occasional gaps in visibility did naturally result in minor and temporary increased organizational risks, the overall volume of non-VPN-connected remote work that took place was so low and infrequent that it was considered to be negligible and ignored. With release 7.3.2, Has anyone “gone rogue”?



















Let's personalize your content