Cuttlefish malware targets enterprise-grade SOHO routers
Security Affairs
MAY 1, 2024
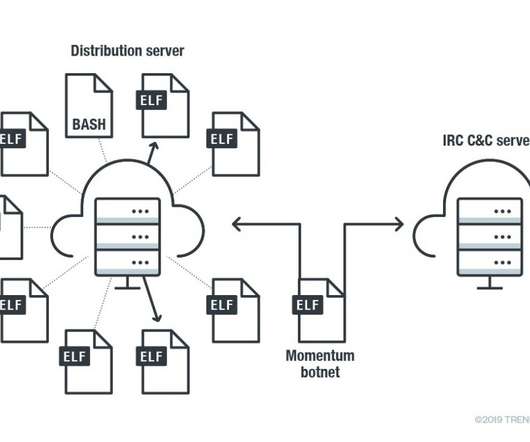
A new malware named Cuttlefish targets enterprise-grade and small office/home office (SOHO) routers to harvest public cloud authentication data. The malware creates a proxy or VPN tunnel on the compromised router to exfiltrate data, and then uses stolen credentials to access targeted resources.
















































Let's personalize your content