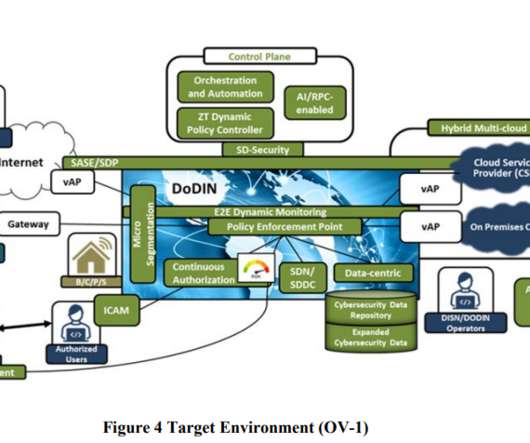
Comment: US Department of Defense Zero Trust Reference Architecture 2.0
Security Boulevard
NOVEMBER 25, 2022
of the US Department of Defence Zero Trust Reference Architecture has been cleared for public release and is a good, detailed read regarding an actual migration and implementation model. The document is available here. The post Comment: US Department of Defense Zero Trust Reference Architecture 2.0 Version 2.0








































Let's personalize your content