News alert: ACM TechBrief lays out risks, policy implications of generative AI technologies
The Last Watchdog
SEPTEMBER 27, 2023
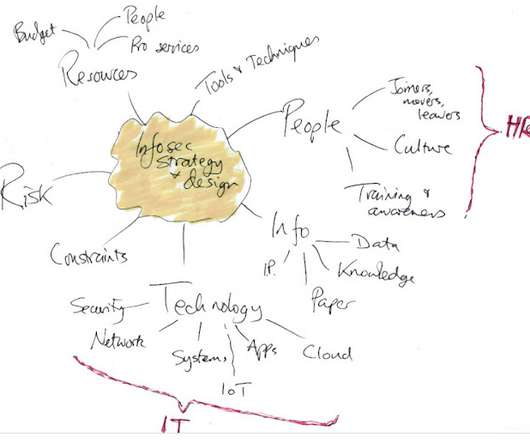
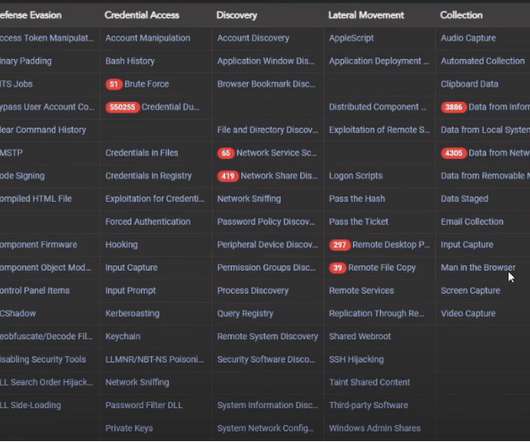
It is the latest in the quarterly ACM TechBriefs series of short technical bulletins that present scientifically grounded perspectives on the impact and policy implications of specific technological developments in computing.

















































Let's personalize your content