Using the LockBit builder to generate targeted ransomware
SecureList
APRIL 15, 2024
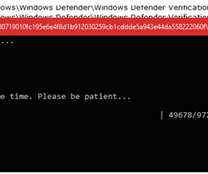
They generated a custom version of the ransomware, which used the aforementioned account credential to spread across the network and perform malicious activities, such as killing Windows Defender and erasing Windows Event Logs in order to encrypt the data and cover its tracks. In this article, we revisit the LockBit 3.0
















































Let's personalize your content