NDR unveiled as essential when complying with the Executive Order
Cisco Security
NOVEMBER 18, 2021
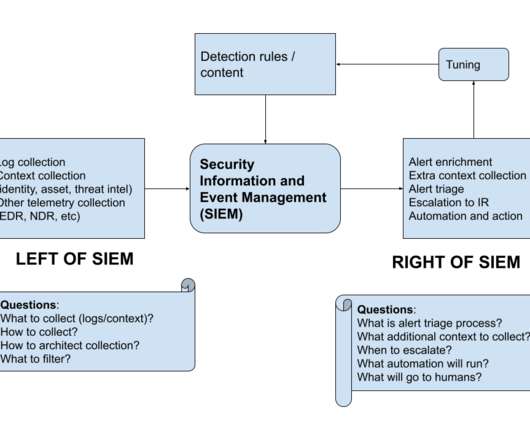
Endpoint detection and response (EDR), multi-factor authentication (MFA), and the need for increased encryption, while implementing a zero-trust approach, were all called out as requirements within the order. While the term NDR is relatively new, the technology is not. See figure 1].


















































Let's personalize your content