Experts found a macOS version of the sophisticated LightSpy spyware
Security Affairs
MAY 30, 2024
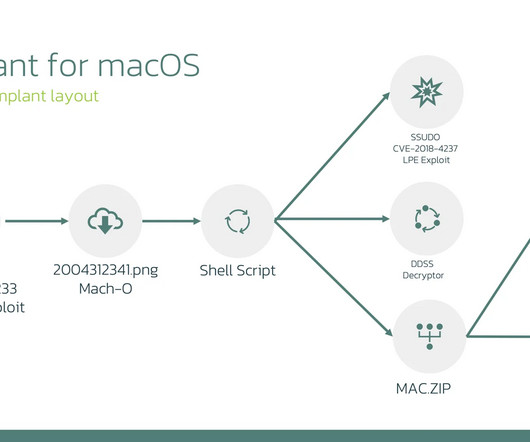
Researchers spotted a macOS version of the LightSpy surveillance framework that has been active in the wild since at least January 2024. LightSpy can steal files from multiple popular applications like Telegram, QQ, and WeChat, as well as personal documents and media stored on the device.



























Let's personalize your content