No, I Won't Link to Your Spammy Article
Troy Hunt
APRIL 6, 2020
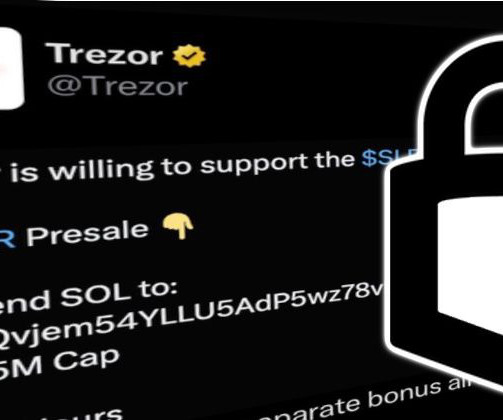
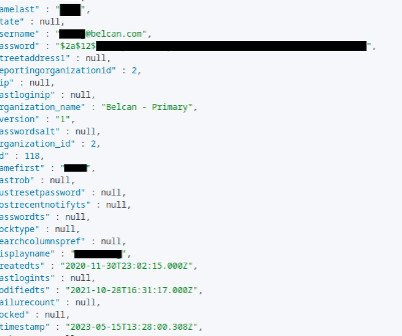
I also have an article on [thing] and I think it would be a great addition to your blog. So now when people search for [thing], they'll hopefully end up here rather than on the spammy article thus penalising you for your behaviour. No, no it wouldn't and there are all sorts of reasons why not. Just the title. On a popular blog.

















































Let's personalize your content